Businesses still face constant cybersecurity threats and risks, making IT risk assessment a crucial part of the security strategy. An IT risk assessment checklist is a structured tool that helps organizations identify, evaluate, and manage risks related to their IT infrastructure. It ensures data security, compliance, and business continuity. By systematically assessing vulnerabilities, companies can prevent breaches proactively, strengthen security measures, and comply with industry regulations such as ISO 27001, NIST, and GDPR.
This checklist covers essential areas, including maintaining an updated asset inventory, identifying threats, prioritizing risks, implementing security controls, and enhancing incident response readiness. Regular updates and involvement from stakeholders further improve security resilience. In this guide, we will explore how an IT risk assessment checklist can protect your business, streamline compliance, and minimize cybersecurity threats.
Table of Contents
What is IT Risk Assessment?
IT risk assessment is the process of identifying, assessing, analyzing, and mitigating risks associated with a company’s IT systems, data, and infrastructure. It manages potential threats, security risks, and vulnerabilities to prevent security threats that may impact business operations and assets. Its main objective is to help you achieve optimal security at a reasonable cost. This can be a great way to gain insight into your business’s IT environment, controls, and risks for improving gaps and recommending remediation or risk mitigation.
With this, you can look for solutions to threats or risks much more easily. IT risk assessment can be performed by both external and internal parties. Likewise, companies have the flexibility to determine their scope as an IT risk assessment is not an audit.
Why Do We Need IT Risk Assessment?
We need an IT risk assessment checklist to identify, evaluate, and mitigate potential threats to a business’s information systems. A well-executed IT risk assessment can discover a business’s weak points and help prevent cyber attacks, data breaches, and other IT-related risks by ensuring security measures are regularly evaluated and in place. By reviewing areas like user access controls, network security, and software vulnerabilities systematically, companies can reduce their chances of unauthorized access and data loss.
Besides security, IT risk assessment also supports regulatory compliance, like the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR). They require businesses to implement strict data protection measures and a checklist to ensure all the necessary policies and procedures are being followed properly. Likewise, in addition to legal compliance, using an IT risk assessment checklist enhances business continuity and disaster recovery plans by identifying critical systems and creating action plans for swift recovery in case of incidents. This ensures minimal downtime by maintaining operations during disruptions and ensures the organization can maintain operations even in the midst of disruptions.
What Are The Key Components Of An IT Risk Assessment Checklist?
Regular risk assessments help organizations identify, and prioritize risks to their operations, and quantify operations, data, and other assets that arise from information systems. Using an IT risk assessment checklist can help you understand your risks and enhance your procedures, technologies, and processes to reduce the chances of financial loss.
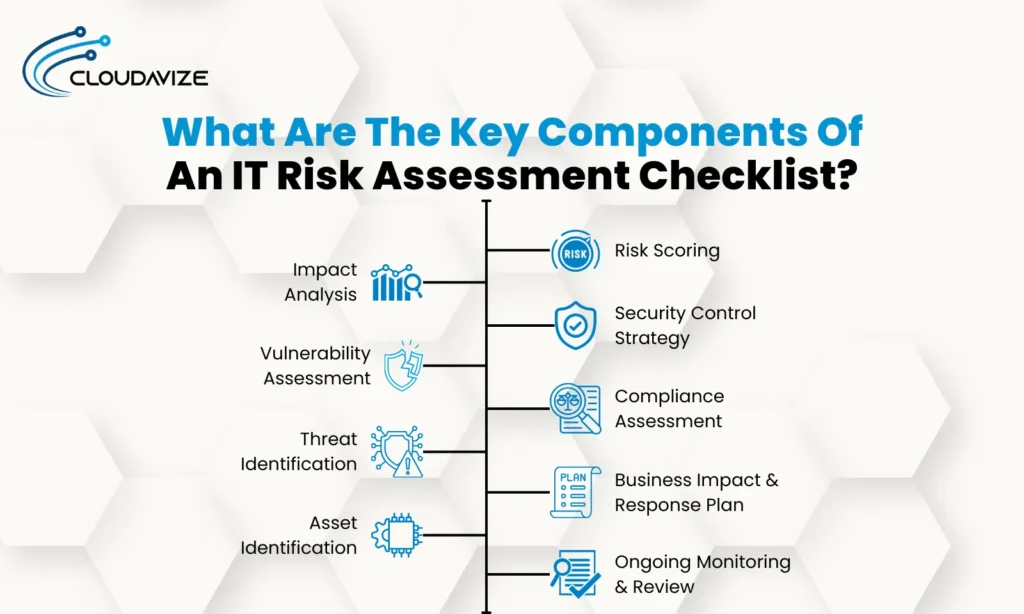
Asset Identification
Firstly, you should create a complete up-to-date inventory of all assets like hardware, software, and data across the business that could be threatened and can result in monetary loss. Some of the other examples are credentials, encryption keys, partner documents, and sensitive and regulated content like medical information and credit card data.
Then, classify each asset according to its level of sensitivity, criticality, and business value to help with risk assessment and guide you in implementing cybersecurity tools. Lastly, analyze your data and IT infrastructure, review documentation, and interview management to identify dependencies between systems to protect assets appropriately.
Threat Identification
Threats that could harm the business, such as internal and external cyber threats, malware, phishing, system failure, malicious human actions, and human error,s such as insider risks that could exploit vulnerabilities within these asset,s should be identified.
Likewise, assess physical security threats such as unauthorized access and hardware theft within these assets. Lastly, monitor regulatory and third-party risks that could impact security compliance.
Vulnerability Assessment
Vulnerability is a weakness that might lead to a breach of information security and harm your company or organization. You can conduct automated vulnerability scans and manual penetration testing using analysis, audit reports, vendor data, information security, evaluation procedures, and automated vulnerability scanning tools.
You can review, inspect, and evaluate security misconfigurations, access controls, and unpatched software
Impact Analysis
Next, you should assess the potential impact of each identified risk to your company in terms of financial, operational, and reputational risks of identified threats. You can conduct a Business Impact Analysis (BIA) to measure potential downtime and data loss to analyze risk impact.
Lastly, assess the probability that each risky scenario might be exploited using factors such as the nature of the vulnerability, hence, prioritize risk scenarios based on severity and likelihood of occurrence.
Risk Scoring
After gathering your assets, you can categorize how likely each of the vulnerabilities of your assets be exploited using the Risk= Asset x Threat x Vulnerability formula. This formula helps you assess each risk and assign it a value of high, moderate, or low.
One of the key differences between quantitive and qualitative analysis is the basis for evaluating risks. While qualitative risk analysis is based on a person’s perception or judgment while quantitative risk analysis is based on verified and specific data.
Risk tolerance refers to the amount of loss an investor is prepared to take while making an investment decision. The risk is determined by several factors like timeline, goals, age, portfolio size, and investor comfort level, that drive an investor to take it.
Security Control Strategy
Security control strategies are measures incorporated into policies, procedures, and standards that are intended to prevent or reduce the probability and the severity of a risky event. As an investor, you should implement preventive controls such as MFA, Encryption, and Firewalls to avoid threats or reduce the likelihood and potential impact of a successful event.
Likewise, you should deploy detective controls like Security Information and Event Management (SIEM) Systems, Intrusion Detection Systems, (IDS), and anomaly detection. There are three main types of IT security and control strategies Technical, administrative, and physical.
Compliance Assessment
Compliance assessment is a critical component of an IT risk assessment checklist as it helps the company identify and mitigate risks associated with failing to comply with legal, industry, or regulatory norms. It ensures adherence to relevant industry regulations and standards such as GDPR, HIPAA, PCI-DSS, or ISO 27001.
By incorporating compliance assessment into the IT risk assessment process, businesses can proactively address potential compliance risks and ensure that their security measures align with regulatory requirements. You can conduct compliance audits and third-party risk assessments.
Business Impact & Response Plan
A business impact & response plan is a crucial component of an IT risk assessment checklist to predict the consequences of a disruption to your business and develop a disaster recovery strategy with offsite backups and failover systems.
This helps businesses understand and quantify the impact of potential disruptions allowing them to develop strategies to mitigate risks and ensure business continuity. They conduct crisis communication planning for breach notifications and legal compliance to reduce potential damage to the business.
Ongoing Monitoring & Review
Ongoing monitoring and review ensure that the implemented control measures are functioning as planned and adapt to any changes in the operations that may affect risk levels. This process continuously monitors threats using real-time security tools and threat intelligence to track the efficiency of current risk control measures.
Effective monitoring and review involve engaging relevant personnel across various levels of an organization to ensure a comprehensive understanding of risks among staff. Regular security awareness training and risk assessments complement this effort by keeping employees informed about potential risks and easily updating security policies and controls based on emerging risks and vulnerabilities.
How Do You Perform An IT Risk Assessment?
IT risk assessment involves several key steps to identify, assess, and mitigate risks to a company’s IT environment. Once the planning and necessary resources are allocated, you can perform two categories of risk assessments, quantitative and qualitative risk assessments. The most effective approach is to incorporate aspects of both of them as both of them allow you to communicate risk with different types of people.
Companies work with multiple teams who are concerned about different things like a legal and financial team will be interested in numbers while operation teams like sales and customers are interested in security events. Following these steps will help you conduct a basic information security risk assessment and provide you with the tools you need to begin building a consistent process for identifying key business risks.

Step 1: Define Scope & Objectives
A risk assessment starts by deciding what is in the scope of the assessment which could cover the entire organization, a business unit, or a specific aspect of the business such as payment processing or a web application. When defining the scope and objectives for an IT risk assessment, several systems, data, and processes are included to ensure a comprehensive evaluation. Next, identify key business goals like the security of IT infrastructure, data protection, regulatory compliance, operational security, and known vulnerabilities of the company.
Step 2: Inventory IT Assets
Assets like hardware, including those in the data center, communication, and network components like desktops, laptops, PDAs, operating systems like PC, network management systems, data repositories such as database management systems and files, security systems like firewalls and intrusion detection systems, and business processes, computer operation processes, network operation processes, and application operation processes are typically included in the IT risk assessment.
Once the assets are finalized, they should be categorized based on criticality and sensitivity. Criticality can be determined by evaluating the asset’s role and its potential financial impact. Categorizing helps ensure each asset is managed appropriately.
Step 3: Identify Threats & Vulnerabilities
Then, the company should identify all the threats and vulnerabilities that can be exploited during a cyberattack. Some of the common vulnerabilities are IT misconfigurations, weak passwords, weak IT settings, excessive administrative and access rights, and unpatched applications or systems. You can conduct threat modeling using a threat library to identify potential risks to help secure systems and data.
You need to take into account some potential physical vulnerabilities when identifying and running vulnerability scans and penetration tests. Likewise, you should also analyze historical security incidents for common risks that can harm your business.
Step 4: Conduct Risk Analysis
After identifying the vulnerabilities in your system, you should implement controls to minimize or eliminate the vulnerabilities and threats. You should evaluate the impact of threats on business operations to eliminate the risk itself or control to address threats that can’t be eliminated.
Risks and threats can be both technical and non-technical, hence, you should use a matrix to classify risks based on severity. Also, rank the risks from low to high to determine their priority level to prioritize actions to mitigate risk.
Step 5: Develop a Risk Mitigation Plan
A risk mitigation plan is a comprehensive strategy used to mitigate risk within an organization. It makes it much easier for organizations to implement risk mitigation internally. The mitigation process is to lessen the negative effects that risks may have on the employee’s safety and the company itself.
Businesses should implement security controls like firewalls, monitoring tools, and MFAs to reduce and mitigate risks. Likewise, organizations should patch vulnerabilities and enforce strict access controls to strengthen the culture of safety within the company. Lastly, businesses should develop incident response and disaster recovery plans to lessen the risk and for a smoother process.
Step 6: Perform Compliance Assessment
Compliance risk assessments identify, prioritize, and control risks associated with the threat of non-compliance in your company. It helps organizations understand their inherent risks and develop appropriate mitigation strategies. By conducting a compliance risk assessment, businesses can map out their processes, transactions, and information systems in a clear view.
Companies should audit internal policies to ensure adherence to GDPR, ISO 27001, HIPAA, and PCI-DSS or other security standards that are tailored to a company’s unique business processes. You should document security practices for regulatory reporting and address risks to avoid encountering them without preparation.
Step 7: Monitor & Review Risks Continuously
Companies should monitor and review the effectiveness of the implemented mitigation strategies as needed and periodically review their performance. You can deploy SIEM tools like Exabeam, Splunk, LogRhythm, IBM QRadar SIEM, SECURONIX, and McAfee for real-time threat detection.
Conduct regular risk assessments and audits as it helps identify inadequacies in current risk management and compliance processes. You should update security policies based on emerging threats to help you manage risks unique to your business.
What Are The Best Practices For Using An IT Risk Assessment Checklist?
The best practices for using an IT risk assessment checklist are to establish clear frameworks, involve key stakeholders, create actionable mitigation plans, involve cross-functional teams, continuously update risk inventories, prioritize risks based on impact and likelihood, foster a culture of risk awareness, and document and review assessments to strengthen company’s technology risk assessment processes leading to more robust risk management and enhanced organizational resilience. By following the best IT risk assessment practices, companies can proactively manage IT risks and strengthen their cybersecurity posture.
Define Scope & Objectives Clearly
Clearly defining the objectives and scope is essential for an effective AI risk assessment. To use an AI risk assessment checklist effectively, identify the systems, data, and processes to be assessed, including AI models and infrastructure. Ensure alignment with business goals and regulations like GDPR and HIPAA. Establish risk tolerance levels using industry standards such as NIST and ISO to prioritize mitigation efforts. A clear scope and objective framework is essential for a focused and compliant AI risk assessment.
Maintain an Updated Asset Inventory
Keeping your asset inventory updated is vital for managing IT risks! Regularly list and categorize your IT assets, including hardware, software, cloud services, and team members. Focus on the key systems that are crucial for your business, as they need additional security measures. Remember to include third-party vendors, too, since they can add extra risks. An updated inventory helps you identify vulnerabilities and strengthens your overall security and incident response.
Use a Structured Approach for Threat & Vulnerability Identification
A structured approach to identifying threats and vulnerabilities can greatly improve IT security. Using threat modeling helps you anticipate attack vectors and understand how threats might exploit system weaknesses. Perform automated vulnerability scans and manual penetration testing to detect security flaws and validate their exploitability. Analyze historical incidents to identify recurring security gaps and improve defenses against known threats. This proactive approach helps organizations strengthen their security posture and mitigate risks effectively.
Assign Risk Scores for Prioritization
Efficiently assigning risk scores helps prioritize threats effectively. You should use a risk matrix such as Likelihood vs. Impact to categorize risks as Low, Medium, High, or Critical, ensuring a structured evaluation. Likewise, focus on high-impact vulnerabilities that could cause data breaches, system downtime, or significant business disruptions. You should document all identified risks and track them over time to monitor progress and measure improvements in security posture. This approach ensures that the most critical risks receive immediate attention, enhancing overall cybersecurity resilience.
Implement a Layered Security Control Strategy
A layered security control strategy strengthens IT defenses by combining multiple protection measures. First, implement preventive controls such as firewalls, multi-factor authentication (MFA), encryption, and endpoint protection to thwart threats before they arise. Then, utilize detective controls like SIEM monitoring, intrusion detection/prevention systems (IDS/IPS), and anomaly detection to spot suspicious activity in real time. If a breach occurs, implement corrective controls like an incident response plan, disaster recovery, and security training to minimize damage. By integrating these layers, organizations can effectively prevent, detect, and respond to cyber threats.
Ensure Compliance with Industry Regulations
Ensuring compliance with industry regulations is essential for data security and effective risk management. To begin, align your IT risk assessment checklist with standards such as ISO 27001, NIST, HIPAA, PCI-DSS, SOC 2, and GDPR to meet both legal and industry requirements. Next, conduct regular compliance audits and document your security policies to monitor adherence and identify any gaps. Additionally, it is also important to assess the security measures of third-party vendors to safeguard the supply chain from potential risks. By following these steps, organizations can enhance regulatory compliance, avoid penalties, and strengthen their overall cybersecurity resilience.
Continuously Monitor & Update the Checklist
For staying ahead of evolving threats, continuously monitoring and updating the IT risk assessment checklist is essential. You should implement real-time threat detection tools such as SIEM, EDR, and XDR to proactively identify and respond to security incidents. Then, you should schedule to conduct quarterly or annual IT risk assessments to evaluate vulnerabilities and measure the effectiveness of your security measures. Additionally, regularly update your checklist to address new cybersecurity threats and emerging compliance requirements. By doing this, businesses can enhance their security, maintain compliance, and effectively minimize cyber risks.
Involve Key Stakeholders & Train Employees
Involving key stakeholders and training employees is crucial for effective IT risk management. To ensure a comprehensive approach, engage IT, security, compliance, and executive teams in risk assessments. To enhance cybersecurity, it is essential to conduct regular security awareness training aimed at reducing human-related risks, such as phishing and social engineering attacks. Likewise, it is also important to assign roles and responsibilities for risk management and mitigation to improve accountability. By prioritizing collaboration and education, organizations can strengthen their cybersecurity defenses and promote a culture of security awareness.
Document & Review Risk Mitigation Actions
Documenting and reviewing risk mitigation actions is one of the crucial steps in strengthening cybersecurity and compliance. First, maintain a comprehensive risk register that tracks identified threats, actions taken, and outcomes to enhance accountability. Likewise, regularly review past assessments to measure progress and refine security strategies based on evolving risks. Moreover, ensure executive buy-in to secure the necessary budget and resources for effective risk management. Follow these steps so your business can enhance threat response, improve security resilience, and maintain regulatory compliance.
Test & Improve Incident Response Readiness
To ensure business continuity and minimize cyber threats, testing and improving incident response readiness is critical. You should conduct tabletop exercises and simulated cyberattack trainings to evaluate response effectiveness and update business continuity and disaster recovery plans based on findings to strengthen durability. Also, you can establish a clear communication plan for security incidents and breach notifications to ensure quick and coordinated responses. By following these steps, businesses and organizations can reduce downtime, enhance cybersecurity, and mitigate overall damage.
How Can Implementing an IT Risk Assessment Checklist Improve Overall Security and Business Resilience?
Implementing an IT risk assessment checklist significantly improves security and business resilience by proactively identifying vulnerabilities before they can be exploited, reducing the risk of security breaches. Similarly, it enhances compliance and governance by ensuring adherence to industry regulations and security standards like ISO 27001 and NIST. Lastly, it strengthens incident response and recovery, helping organizations prepare for cyber threats and minimize downtime, improve threat detection, regulatory compliance, and overall operational stability. And if you’re looking to streamline your IT risk assessment, link up with CloudAvize and experience a smooth and tailored solution according to your security needs. We offer expert solutions to help you stay ahead of threats, risks, and help you improve cybersecurity and meet industry standards with confidence.



