Data security is paramount in the digital age, driven by the increasing volume of sensitive information stored and transmitted online. It offers benefits such as competitive advantage through enhanced customer trust, prevention of financial losses, and operational resilience via robust backup strategies. Key components include encryption, which secures data; data erasure, ensuring safe deletion; and data masking, obscuring sensitive information. It reduces breach risks, supports regulatory compliance, and fosters ethical data handling. According to IBM’s Cost of a Data Breach Report 2023, the average time to identify and contain a data breach is 277 days, emphasizing the importance of robust security measures to mitigate risks and financial losses.
Tools like DLP software, IDPS, and IAM systems ensure data protection, while strategies like zero trust architecture, automated compliance reporting, and cloud security measures address emerging threats. Effective measures, such as access controls, backups, and disaster recovery plans, prevent data breaches, mitigate financial and reputational damage, and ensure compliance with regulations like GDPR and HIPAA. AI-driven threat detection and zero-trust architecture reshape the data security landscape. Organizations can depend on managed service providers to safeguard sensitive data and maintain business continuity. MSPs integrate data security services with identity management and provide enterprise-grade solutions.
Table of Contents
What is Data Security?
Data security is the practice of protecting digital information from unauthorized access, corruption, or theft throughout its lifecycle. The primary goals of data security are to ensure the confidentiality, integrity, and availability of data. Various components that constitute data security include encryption, which converts data into a coded format; data erasure, which securely removes data from storage devices; and data masking, which obscures specific data within a database. Effective data security measures also involve implementing robust access controls, regular backups, and comprehensive disaster recovery plans to safeguard sensitive information.
The impact of data breaches on businesses and individuals can be severe, leading to financial losses, reputational damage, and legal consequences. According to Symantec, IoT devices experience an average of 5,200 attacks per month, underscoring the pervasive threat landscape. Furthermore, InsuranceBee’s survey highlights that 83% of small and medium-sized businesses (SMBs) are not financially prepared to recover from a cyber attack, highlighting the critical need for effective data security strategies. Data breaches can erode customer trust and result in fines for non-compliance with regulations such as GDPR and HIPAA, making robust data security practices indispensable for business continuity and legal compliance.
Why is Data Security Important?
Data security is important because it protects sensitive information from unauthorized access, corruption, or theft, ensuring business continuity and customer trust. Protecting personal data, intellectual property, and financial information is crucial for maintaining operational integrity and avoiding significant financial losses, reputational damage, and legal ramifications. Data breaches can devastate businesses, which is highlighted well by MetaCompliance’s research. It shows that up to a third of retail, finance, and healthcare customers will stop doing business with organizations that have been breached, and 85% will share their experience. Moreover, compliance with data protection regulations like GDPR, HIPAA, and Payment Card Industry Data Security Standard (PCI DSS) is essential to avoid hefty fines and maintain legal standing.
The significance of data security extends beyond mere protection; it also provides a competitive advantage by enhancing customer trust and loyalty. The 2024 CrowdStrike Global Threat Report highlights the evolving threat landscape, including a 75% increase in cloud intrusions and the emergence of new types of cyber-attacks and vulnerabilities. Organizations have ethical and social responsibilities to protect data, reinforcing their commitment to customers and stakeholders. Effective data security measures help businesses stay ahead of these threats, safeguard their reputation, and ensure compliance with stringent data protection regulations, solidifying their market position.
Benefits of Data Security
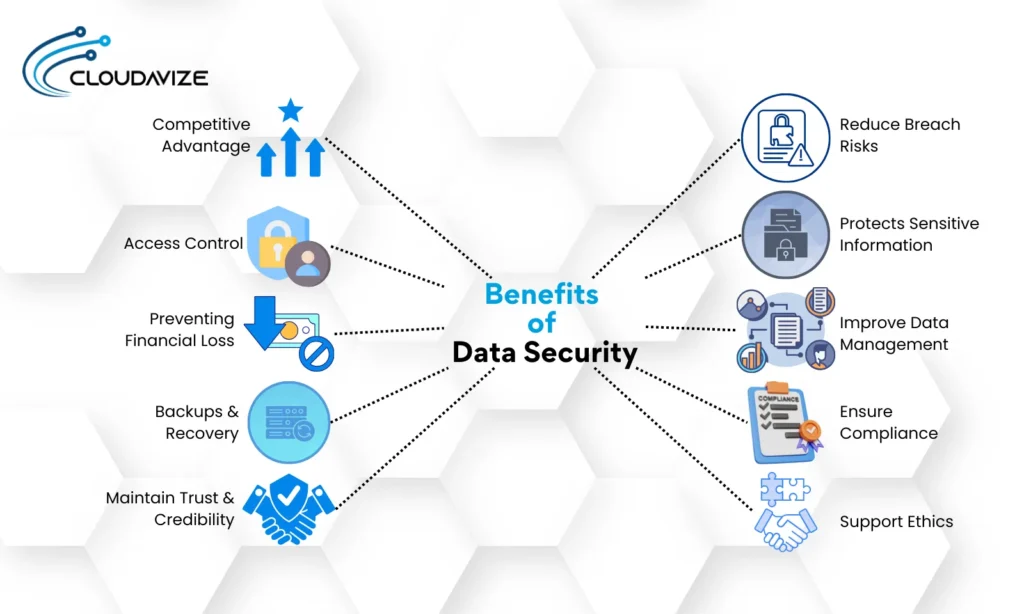
Benefits of robust data security measures range from protecting sensitive information to enhancing business operations. Effective data security ensures data confidentiality, integrity, and availability, which supports business continuity, regulatory compliance, and ethical data handling.
- Competitive Advantage
Robust data security provides a competitive edge by enhancing customer trust and loyalty. Customers are more likely to engage with businesses that demonstrate a strong commitment to protecting their personal information. Additionally, companies with strong data security measures can differentiate themselves in the marketplace, attracting more security-conscious clients and partners.
- Access Control
Access control is crucial in protecting sensitive information. Methods like multi-factor authentication (MFA) and role-based access control (RBAC) ensure that only authorized users can access critical data, reducing the risk of internal threats. These methods help monitor and audit user activities, providing an extra layer of security and accountability within the organization.
- Preventing Financial Loss
The financial implications of data breaches can be severe, encompassing costs related to breach containment, legal fees, regulatory fines, and loss of revenue. Data security measures such as encryption, intrusion detection systems, and regular security audits help prevent these breaches, thereby avoiding substantial financial losses. According to IBM, the breach cost savings were USD 2.66 million for organizations with an incident response (IR) team and regularly tested IR plan compared to no team or testing. Implementing strong data security protocols protects against immediate financial repercussions and safeguards long-term profitability by maintaining business continuity and customer trust.
- Backups And Disaster Recovery
Regular data backups and a solid disaster recovery plan are crucial for data resiliency. Organizations should implement a backup strategy that involves frequent full and incremental backups, leveraging technologies like deduplication and compression to optimize storage and bandwidth utilization. The importance of data backups is highlighted by the fact that 73% of manufacturing companies used data backups to restore data after a ransomware attack. A well-designed disaster recovery plan outlines recovery procedures, failover mechanisms, and periodic testing to restore data and systems promptly, minimizing downtime and operational disruptions.
- Helps Maintain Trust And Credibility
Implementing robust data security measures is paramount for safeguarding sensitive information from unauthorized access, ensuring data integrity, and maintaining compliance with regulatory standards. They encompass encryption, access controls, and secure protocols, mitigating data breaches, reputational damage, and legal risks. A comprehensive data security strategy enables business continuity, maintains customer trust, enhances credibility, and fosters long-term stakeholder confidence.
- Lowering Data Breach Risks
Robust data security strategies significantly reduce the risk of data breaches by implementing comprehensive protective measures against cyber threats. These measures encompass proactive safeguards like encryption, access controls, secure data handling protocols, and reactive incident response mechanisms to promptly detect, contain, and remediate potential breaches. A strong data security posture, backed by risk assessments, security training, and regular testing, fosters a resilient cybersecurity culture that protects sensitive information and maintains compliance.
- Protects Sensitive Information
Data security safeguards critical information assets from unauthorized access, modification, or disclosure, fortifying organizational trust and compliance. Its robust encryption mechanisms and access controls mitigate the risks of data breaches and cyber threats, preserving the confidentiality, integrity, and availability of sensitive data. Organizations can protect their intellectual property, customer data, and operational resilience by implementing a comprehensive data security framework, ensuring business continuity and maintaining a competitive edge.
- Better Data Management
Robust data security protocols facilitate meticulous data governance, mitigating risks of data breaches and ensuring regulatory compliance. Encryption, access controls, and auditing mechanisms fortify data integrity and confidentiality. Rigorous data lifecycle management strategies optimize data utilization, enabling informed decision-making and competitive advantages.
- Meeting Compliance Requirements
Data security facilitates adherence to stringent regulations like GDPR, HIPAA, and PCI DSS. Robust data protection measures help organizations mitigate legal risks and financial penalties, as HIPAA compliance failure can result in fines of up to $50,000 per offense, a maximum annual fine of $1.5 million, and a potential prison term of up to 10 years, according to The HIPAA Journal. Comprehensive security protocols enable enterprises to operate within regulatory boundaries and expand globally.
- Support Ethics
Ethically, data security underscores responsible data handling, ensuring that organizations respect the privacy and integrity of their customers’ information. Employing robust encryption, access controls, and incident response safeguards customer data. Organizations demonstrating commitment to data security foster trust and customer loyalty.
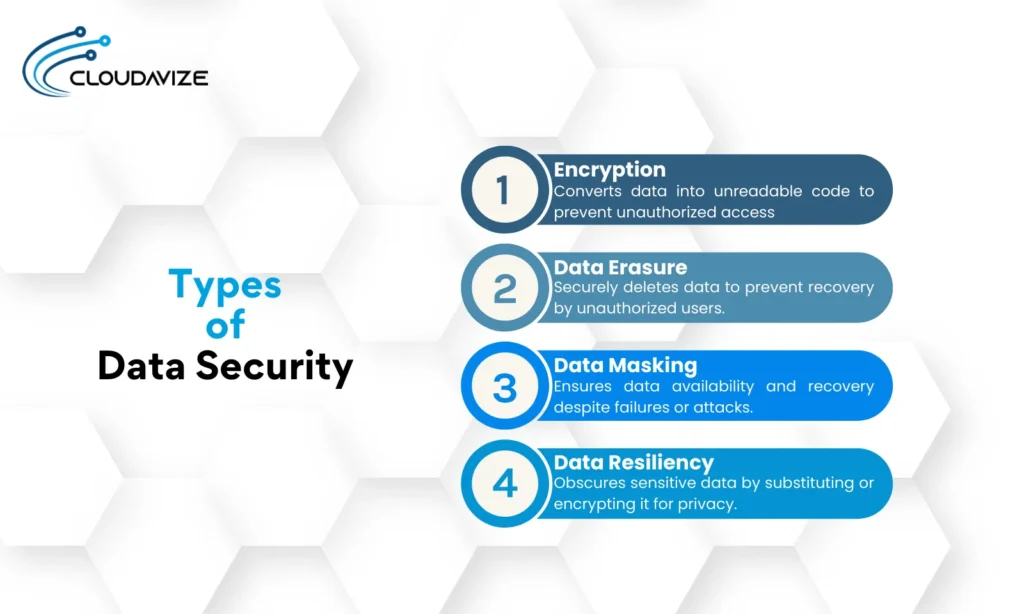
Types of Data Security
Types of data security involve encryption, data erasure, data masking, and data resiliency, each addressing different aspects of data integrity and confidentiality.
Encryption
Encryption includes converting data into a coded format to prevent unauthorized access. It converts data into a coded format that is unreadable without a decryption key, much like a secret code that only those with the key can understand. The basic mechanics of encryption involve algorithms and encryption keys, which transform plaintext data into ciphertext.
There are two main types of encryption: symmetric encryption and asymmetric encryption, where symmetric requires the same key for encryption and decryption and asymmetric which uses a pair of public and private keys. Typical encryption applications include securing communications, such as emails and instant messages, and protecting stored data on devices and cloud storage systems. Encryption significantly enhances data confidentiality and security by making data unreadable without the appropriate decryption key.
Data Erasure
Data erasure is the process of securely removing data from storage devices, ensuring that unauthorized users cannot recover or access it. In simple terms, it means securely deleting data so it can’t be recovered, similar to shredding documents before discarding them.
The primary data erasure methods are overwriting, degaussing, and physical destruction. Overwriting replaces old data with new data multiple times, degaussing uses magnetic fields to erase data on magnetic storage devices, and physical destruction involves breaking the storage device to prevent data retrieval. Regulations governing data erasure practices, such as GDPR and HIPAA, require businesses to dispose of sensitive information securely. Benefits of data erasure include preventing data breaches and ensuring compliance with data protection laws, thereby safeguarding organizational and customer data.
Data masking
Data masking is the process of obscuring specific data within a database to protect sensitive information. Different data masking techniques include substitution, shuffling, and encryption. Substitution replaces real data with fake data, shuffling rearranges data, while encryption makes data unreadable.
Data masking is commonly used in software development and testing scenarios, replacing real data with masked data to maintain data privacy. The benefits of data masking include protecting sensitive information, reducing the risk of data breaches, and enabling organizations to use realistic datasets without exposing actual data.
Data resiliency
Data resiliency is the ability to withstand and recover from data-related incidents, ensuring that data remains available and intact despite failures or attacks. Strategies for achieving data resiliency include regular backups, redundant systems, and disaster recovery plans. Regular backups create copies of data at scheduled intervals. Redundant systems provide alternative systems that can take over in case of failure. Disaster recovery plans outline procedures for restoring data and operations after a catastrophic event.
Technologies that support data resiliency include cloud storage, data replication, which duplicates data across multiple locations, and automated failover systems, which automatically switch to backup systems in the event of a failure. Benefits of data resiliency include minimizing downtime, ensuring business continuity, and protecting against data loss, thereby enhancing the overall security posture of an organization.
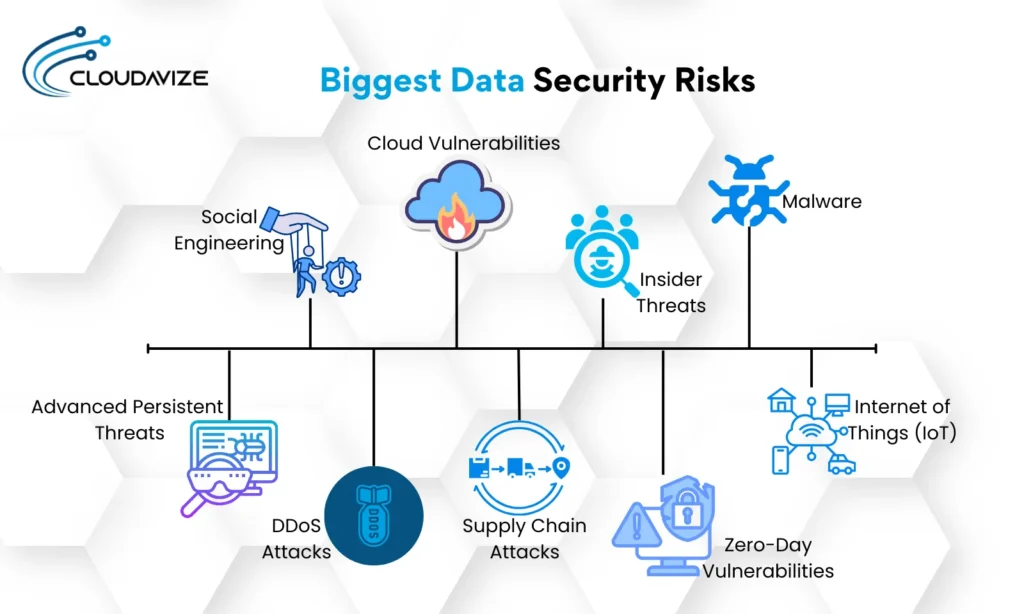
What Are The Biggest Data Security Risks?
Biggest data security risks include social engineering, cloud vulnerabilities, insider threats, malware, and APTs. It also involves DDoS and supply chain attacks, zero-day vulnerabilities, and the Internet of Things.
Understanding and mitigating data security risks is crucial for protecting sensitive information and maintaining business continuity. Some notable data breaches are the 2013 Adobe Data Breach, the 2014 Home Depot Data Breach, the 2017 Equifax Data Breach, the 2013/14 Yahoo Data Breach, and the 2018 Marriott Data Breach. Identifying the data security risks allows organizations to implement effective preventive measures, reducing the likelihood of data breaches and their associated consequences.
Social Engineering
Social engineering is the manipulation of individuals to gain unauthorized access to information. Common techniques include phishing, where attackers pose as legitimate entities to steal sensitive data; pretexting, which involves creating fabricated scenarios to obtain information; baiting, which lures victims with promises of rewards; and tailgating, where unauthorized individuals follow authorized personnel into restricted areas. The $100 million Google and Facebook Spear Phishing Scam, the 2019 deepfake attack on a UK energy company, the 2021 Oversea-Chinese Banking Corporation (OCBC) phishing saga, and the $75 million Belgian Bank Whaling Attack are some of the real-world examples of social engineering attacks.
Potential consequences of social engineering attacks include data breaches and financial losses. Preventive measures include employee training and awareness programs to effectively recognize and respond to these threats.
Cloud Vulnerabilities
Cloud vulnerabilities refer to security weaknesses in cloud computing environments. Common vulnerabilities include misconfigurations, lack of encryption, and insecure Application Programming Interfaces (APIs). These weaknesses can lead to data breaches and loss of data integrity. Strategies for mitigating cloud vulnerabilities include regular security audits, implementing encryption for data at rest and in transit, and ensuring proper configuration and secure access to APIs.
Insider Threats
Insider threats are security risks posed by individuals within the organization. These can include malicious insiders with intent to harm, negligent insiders who unintentionally cause damage, and compromised insiders manipulated by external attackers. Potential consequences of insider threats include data loss and operational disruption. Preventive measures involve implementing strict access controls, continuous monitoring, and employing behavioral analysis tools to detect suspicious activities.
Malware
Malware is malicious software designed to damage, disrupt, or gain unauthorized access to systems. Different types of malware include viruses, which attach themselves to clean files and spread; worms, which replicate themselves to spread to other computers; ransomware, which encrypts data and demands payment for decryption; and spyware, which gathers information without user consent. Potential consequences include data loss and system downtime. Preventive measures include using antivirus software, updating systems and applications, and educating users about safe practices.
Advanced Persistent Threats (APTs)
APTs are prolonged and sophisticated cyber attacks aimed at stealing sensitive data or gaining unauthorized access to systems. Common techniques include targeted phishing emails, exploiting software vulnerabilities, and moving laterally within networks to access critical information., which can lead to data theft, intellectual property loss, and prolonged disruption. Some renowned ATPs that occurred in the past include GhostNet, Stuxnet, Deep Panda (2015), APT28 (2014), APT34 (2017), and APT37 (2012). Preventive measures include network monitoring, intrusion detection systems, and comprehensive employee training programs to recognize and prevent these sophisticated attacks.
DDoS Attacks
Distributed denial-of-service (DDoS) attacks attempt to overwhelm a system, service, or network with traffic to disrupt normal operations. Different methods of DDoS attacks include volumetric attacks, protocol attacks, and application layer attacks, which can potentially cause service downtime, loss of revenue, and reputational damage. Some well-known DDoS attacks are the Novel DDoS attack (2023), the Google Attack (2020), the AWS DDoS attack (2020), and the Mirai Dyn DDoS attack (2016). It can be avoided by deploying DDoS protection services, implementing rate limiting, and designing a robust network architecture to withstand high traffic volumes.
Supply Chain Attacks
Supply chain attacks target an organization’s supply chain to compromise its systems and data. Methods include compromising software updates, exploiting third-party vendors, and inserting malicious code into legitimate software. Some companies that have been victims of Supply Chain attacks in the past include British Airways, Atlassian, Apple, Microsoft, Kaseya, and SolarWinds. The potential consequences of such attacks are data breaches, operational disruptions, and a significant loss of customer trust. Organizations should implement rigorous vendor risk management to prevent these attacks, adopt secure software development practices, and thoroughly vet all third-party services.
Zero-Day Vulnerabilities
Zero-day vulnerabilities are software flaws that attackers discover and exploit before developers can address them. These vulnerabilities are called “zero-day” because developers have had zero days to patch or fix them. Attackers use these weaknesses to gain unauthorized access to systems before any defenses can be implemented. The implications of zero-day attacks are severe, potentially leading to data breaches, compromised data integrity, and system security failures. To defend against these threats, organizations must adopt proactive measures such as regular software updates, continuous vulnerability scanning, and advanced threat detection systems that can identify and mitigate unknown threats.
Internet of Things (IoT)
The Internet of Things (IoT) is a network of connected devices that collect and exchange data, presenting significant security risks. These risks include weak authentication mechanisms, unpatched vulnerabilities, and unsecured communication pathways. Vulnerabilities can lead to unauthorized system access, data breaches, and even the takeover of critical infrastructure. To mitigate these threats, it is essential to enforce robust authentication protocols, perform regular firmware updates, and maintain secure communication practices for all IoT devices.
What are the Key Components of a Data Security Solution
Key components of a data security solution include Data Loss Prevention (|DLP), Intrusion Detection and Prevention Systems (IDPS), Identity and Access Management (IAM), backup and recovery, Security Information and Event Management (SIEM), and Governance, Risk, and Compliance (GRC). A comprehensive data security solution is crucial for protecting sensitive information, maintaining business continuity, and ensuring compliance with regulatory standards to safeguard digital assets from internal and external threats.
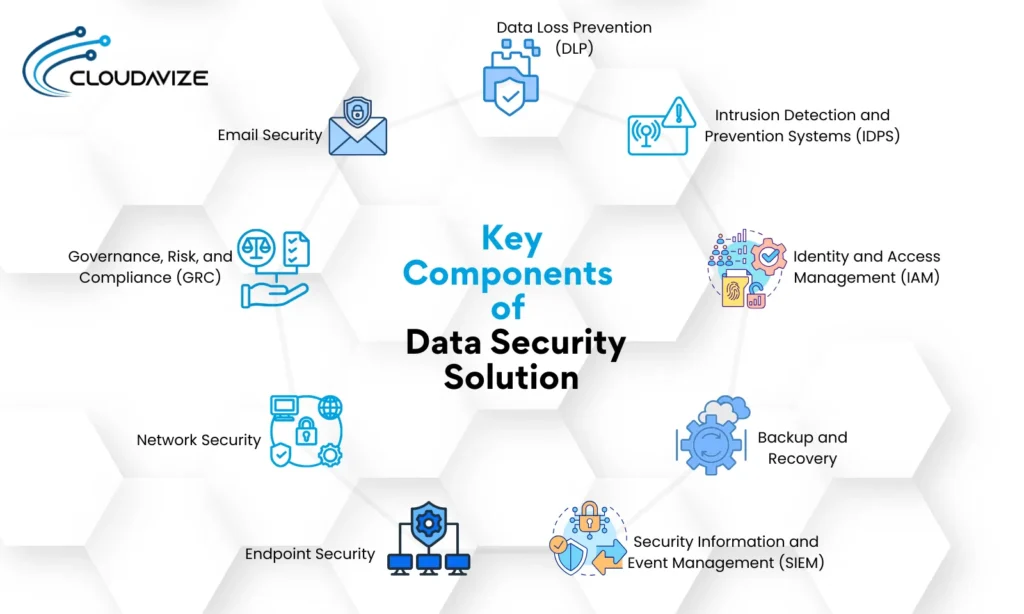
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a strategy to prevent sensitive data from being lost, stolen, or accessed by unauthorized users. DLP mechanisms include monitoring, filtering, and blocking data transfers. Implementing DLP starts by identifying sensitive data, setting up monitoring systems, and configuring rules to prevent unauthorized access. The benefits of DLP include protecting intellectual property and ensuring regulatory compliance by avoiding data breaches and unauthorized data dissemination.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) are tools that monitor network traffic for suspicious activity and take action to prevent breaches. IDPS mechanisms involve signature-based detection, anomaly detection, and automated responses. The benefits include real-time threat detection and enhanced network security, helping organizations respond swiftly to potential threats.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a framework for managing digital identities and controlling access to resources. IAM mechanisms include authentication and authorization, such as multi-factor authentication (MFA) and role-based access control (RBAC). The benefits of IAM include enhanced security, improved compliance, and streamlined access management.
Backup and Recovery
Backup and recovery processes ensure data availability and integrity in case of data loss or system failure. Mechanisms involved in backup and recovery include regular data backups, offsite storage, and detailed recovery procedures. It helps to minimize downtime, maintain data integrity, and ensure business continuity. Ensure you have regular backups stored offsite and conduct periodic recovery tests to confirm data integrity.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) solutions provide real-time analysis of security alerts and data logs through data aggregation, correlation, and automated alerting. The benefits are improved threat detection, compliance reporting, and faster incident response, making managing and mitigating security incidents more manageable.
Endpoint Security
Endpoint security involves protecting devices like computers and mobile devices from security threats using various tools and strategies such as antivirus software, firewalls, and encryption. Additional measures like Endpoint Detection and Response (EDR) for monitoring activities, patch management for updating software, and device management for enforcing security policies enhance protection. Network Access Control (NAC) ensures only secure devices gain access to the network. Together, these measures strengthen device protection, improve data security, and ensure compliance with security standards.
Network Security
Network security measures protect infrastructure from unauthorized access and cyber threats by using firewalls to block malicious traffic, intrusion prevention systems (IPS) to detect and prevent attacks, and network segmentation to isolate sensitive data. These methods secure data transmission, reduce breach risks, and ensure regulatory compliance, safeguarding the network’s integrity and confidentiality.
Governance, Risk, and Compliance (GRC)
Governance, Risk, and Compliance (GRC) is an integrated approach to managing governance, risk management, and compliance. GRC components include policy management, risk assessment, and compliance monitoring. This approach ensures that all governance, risk, and compliance aspects are addressed cohesively, supporting organizational integrity and regulatory adherence.
Email Security
Email security protects communications from phishing, malware, and unauthorized access. Common threats include phishing, spear-phishing, email spoofing, and malware, which can compromise sensitive information. Organizations use spam filters, email encryption, and authentication protocols to counter these threats. Encryption ensures that only intended recipients can read the content, maintaining the confidentiality and integrity of messages. Robust email security prevents data breaches, maintains customer trust, and ensures regulatory compliance. Following best practices—such as using strong passwords, enabling two-factor authentication, and regularly updating security software—further enhances email protection.
Data Security Capabilities and Tools
Data security capabilities and tools involve Database Security Software, Data-Centric Security Software, Data Center Security Solutions, and Data Loss Prevention (DLP) Software. They are essential for protecting sensitive information, ensuring compliance, and maintaining data integrity to address different aspects of data security, from database protection to data loss prevention.
Database Security Software
Database security software includes tools to protect databases from threats like SQL injection, unauthorized access, and data breaches. Tools such as HashiCorp Vault and Oracle Data Safe offer features that prevent data breaches, ensure compliance, and maintain data integrity.
- HashiCorp Vault
HashiCorp Vault helps manage and secure access to secrets and sensitive data. It provides encryption services, access control, and detailed audit logs to ensure data protection and regulatory compliance. It is available in HCP Vault Secrets, HCP Vault Dedicated, and Enterprise. The price for the Dedicated package starts at $1.58 per hour.
- Oracle Data Safe
Oracle Data Safe enhances database security through activity auditing, user assessment, and data masking. It helps organizations monitor database activity, identify security risks, and apply necessary protections to sensitive data. Oracle Data Safe is included with Oracle Cloud Infrastructure database services, which range from $54 to $1,734, depending upon the type of service needed.
Data-Centric Security Software
Data-centric security software focuses on protecting the data itself rather than the systems around it. Principles such as encryption, tokenization, and data masking are employed to safeguard financial data, personal information, and intellectual property.
- Egnyte
Egnyte offers comprehensive data security and management solutions for enterprises. Features include secure file sharing, real-time data monitoring, and automated compliance reporting. These capabilities help organizations protect sensitive data, ensure regulatory compliance, and streamline data management processes. Pricing for Egnyte starts at $20 per user per month. It is available in Business, Enterprise Lite, and Enterprise plans.
- Microsoft Purview Information Protection
Microsoft Purview Information Protection provides tools to classify, label, and protect sensitive information across Microsoft 365 services. Its features include data discovery, policy enforcement, and real-time monitoring, enabling organizations to safeguard their data and comply with regulatory requirements effectively.
Data Center Security Solutions
Data center security solutions protect data centers from physical and cyber threats. Key functionalities include network security, physical security, and access control.
- FortiGate NGFW
FortiGate NGFW provides advanced data center security with features like deep packet inspection, intrusion prevention, and integrated threat intelligence. These capabilities help detect and mitigate threats in real time, ensuring robust protection for data centers. Per the NSS Labs NGFW Comparative TCO Report, Fortinet cost $2 per protected Mbps, while it was as high as $57 per protected Mbps from other NGFW vendors.
- Symantec Data Center Security
Symantec Data Center Security offers comprehensive protection through advanced security measures and monitoring. Its advanced security measures ensure continuous protection against evolving threats, maintaining the integrity and availability of data. You can get Symantec Data Center Security Server Advanced at $539/year for the initial subscription license and support.
Data Loss Prevention (DLP) Software
DLP software prevents the unauthorized transfer or loss of data, ensuring sensitive information remains secure and compliant with data protection regulations.
- Avanan Cloud Email Security
Avanan Cloud Email Security provides robust protection against data loss through email channels. Features include advanced phishing detection, malware protection, and data encryption, which secure sensitive information transmitted via email. They offer Protect, Advanced Protect, and Complete Protect plans for Email Only and Email & Collaboration packages. Pricing for Avanan Cloud Email Security is available upon request.
- Coro Cybersecurity
Coro Cybersecurity offers comprehensive DLP solutions with features like automated threat detection, real-time monitoring, and incident response. These automated systems ensure continuous protection against data loss and cyber threats, safeguarding sensitive data across the organization. Various suites, including Coro Essentials, Endpoint Protection, Email Protection, and SASE, are available at a monthly price of $7.50. Yearly subscription costs $6/month.
Data Security Trends
Data security trends include AI, multi-cloud security, quantum, zero trust architecture, and automated compliance reporting. Staying updated with data security best practices and their latest trends is crucial for protecting sensitive information and ensuring compliance. As cyber threats evolve, understanding and implementing the latest security measures can significantly enhance an organization’s security posture.
AI
AI simulates human intelligence in machines to enhance data security measures. Applications include machine learning for anomaly detection, AI-driven threat intelligence, and automated incident response. According to a recent survey by MarketsandMarkets, AI in the cybersecurity market is projected to grow at a CAGR of 21.9% and hit $60.6 billion by 2026, driven by the increasing adoption of AI-powered security solutions for threat detection and response. Benefits include improved threat detection accuracy, reduced response times, and an enhanced security posture, making AI an invaluable tool in modern data security strategies.
Multicloud security
Multicloud security involves securing data and applications across multiple cloud environments. Challenges include data fragmentation, inconsistent security policies, and increased attack surfaces. Solutions use unified security management platforms, cloud-native security tools, and integrated compliance frameworks to manage and secure data across diverse cloud environments.
Quantum
Quantum computing leverages quantum mechanics to perform complex calculations, posing new threats to data security, such as the potential to break current encryption algorithms. According to MarketsandMarkets, the Global Quantum Computing market was valued at US$1.3 billion in 2024 and is anticipated to be US$5.3 billion by 2029, growing at a CAGR of 32.7% during the forecast period. To protect data against these emerging threats, defenses include developing quantum-resistant encryption algorithms, quantum key distribution, and ongoing research in quantum cryptography.
Zero Trust Architecture
Zero Trust Architecture is a security model that assumes no implicit trust and continuously verifies every access request. Principles include least privilege access, micro-segmentation, and continuous monitoring. Implementation steps involve defining the protected surface, implementing strong authentication, and leveraging advanced threat detection technologies to enhance security.
Automated Compliance Reporting
Automated compliance reporting uses automation to streamline the compliance reporting process. Benefits include increased accuracy, reduced manual effort, and real-time compliance monitoring. Tools such as compliance management software, automated audit trails, and integrated compliance dashboards help organizations maintain compliance efficiently and effectively.
How does data security integrate with different security components?
Data security integrates with various security components by aligning protective measures with broader security solutions, ensuring comprehensive protection. This integration involves coordination with firewalls, intrusion detection systems, identity management, and endpoint protection, enhancing overall organizational security.
Enterprise-Grade Data Security Strategies
Enterprise-grade data security strategies involve comprehensive measures to protect data across large organizations. These strategies integrate data security with various security solutions, such as firewalls, intrusion detection systems, and endpoint protection. Compliance and governance play crucial roles in enterprise data security, ensuring adherence to regulations like GDPR and HIPAA. Incident response planning is also vital for managing and mitigating data breaches and other security incidents, providing a robust defense against potential threats.
Cloud Data Security Measures
Cloud data security measures are strategies aimed at protecting data in cloud environments. Cloud Access Security Brokers (CASBs) play a key role in securing data access and enforcing security policies within the cloud. Encryption and key management are essential for protecting cloud data and ensuring that sensitive information remains secure. The shared responsibility model emphasizes that cloud providers and customers have security responsibilities, requiring collaboration to maintain a secure cloud environment.
BYOD (Bring Your Own Device) Data Security
BYOD data security involves measures to protect data accessed and stored on personal devices used for work purposes. Mobile Device Management (MDM) is crucial for managing and securing mobile devices within a BYOD policy. Endpoint security is also essential for protecting data on personal devices, ensuring that data remains secure despite using non-corporate hardware. Implementing secure access controls is critical to managing data access on individual devices preventing unauthorized access and potential data breaches.
Data Security and Identity Management Integration
Integrating data security and identity management coordinates data protection measures with identity verification processes. Identity and Access Management (IAM) systems manage user identities and control access to data, ensuring that only authorized individuals can access sensitive information. Multi-factor authentication (MFA) enhances security by requiring multiple verification forms, adding an extra layer of protection. Privileged Access Management (PAM) controls and monitors privileged users’ access to critical systems and data, further strengthening data security.
Data Security vs Data Privacy
Data security involves measures to protect data from unauthorized access, corruption, or theft, which are crucial for safeguarding sensitive information and maintaining business continuity, while data privacy is about the right of individuals to control how their personal information is collected, used, and shared.
Data security protects data from threats through technological solutions such as encryption, access controls, and intrusion detection systems. This responsibility generally falls to IT and security teams, who implement these measures to shield organizational data from breaches and cyber-attacks.
Meanwhile, data privacy is essential for building customer trust and ensuring compliance with data protection regulations like GDPR and HIPAA. Data privacy involves legal and regulatory considerations, overseen by legal and compliance teams, to ensure that personal information is handled correctly. Effective data security measures are vital in supporting data privacy by protecting personal data from unauthorized access.
The challenges in managing data security and privacy include preventing data breaches, ensuring regulatory compliance, and balancing robust security measures with user privacy needs. Best practices for data security involve implementing encryption, access controls, and regular security audits, while data privacy best practices include data minimization, obtaining user consent, and ensuring transparency. By integrating strong data security protocols with stringent data privacy practices, organizations can protect sensitive information, comply with regulations, and build customer trust.