Cyberattacks are malicious and deliberate attempts to damage, destroy, or alter information systems and their components. Cybercriminals exploit network, software, or human behavior vulnerabilities to gain unauthorized access or disrupt operations. These attacks can target individuals, businesses, or governments, often aiming to steal sensitive data or sabotage critical infrastructure.
Cyberattacks involve various methods to compromise systems and data. Malware uses malicious software to disrupt and access systems. Phishing tricks users into sharing sensitive information through fraudulent communication. Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks overload networks with traffic, causing disruptions. Man-in-the-Middle (MitM) attacks intercept communications to steal or manipulate data. SQL Injection targets databases to access or modify sensitive information. Password Attacks exploit weak or reused credentials, compromising systems. Social Engineering manipulates human behavior to gain unauthorized access. These attacks lead to data breaches, operational downtime, financial losses, and reputational harm. Implementing robust security measures, user training, and managed services can reduce these risks.
Table of Contents
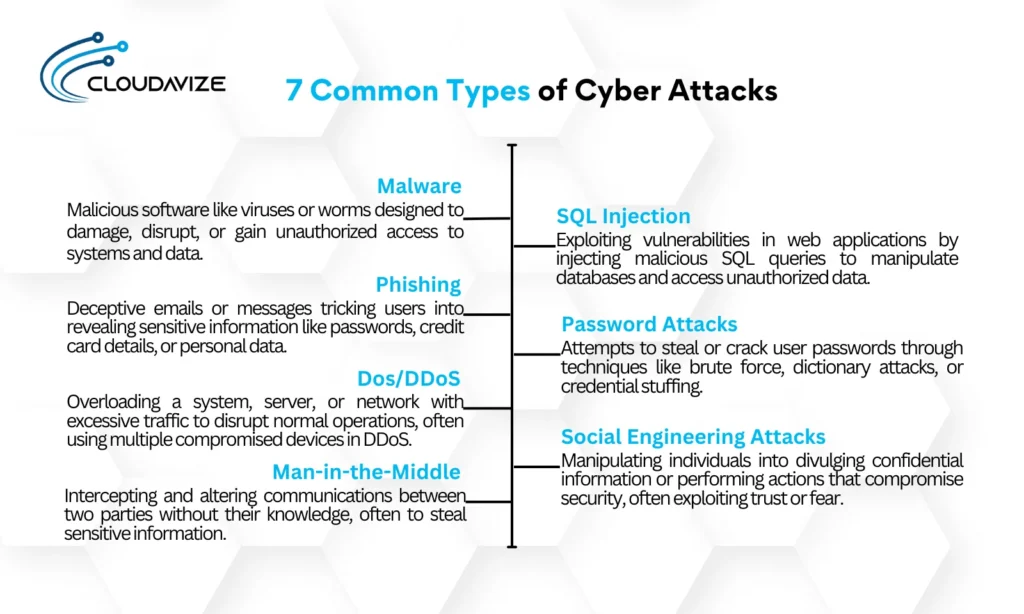
7 Common Types of CyberAttacks
The 7 common types of cyber attacks are as follows:
- Malware
- Phishing
- Denial of Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
- Man-in-the-Middle (MitM) Attacks
- SQL Injection
- Password Attacks
- Social Engineering Attacks
1. Malware
Malware or Malicious Software is intrusive software that spreads by attaching itself to legitimate programs. It contains malicious code that performs harmful actions on the infected system. Malware attacks disrupt and gain unauthorized access to computer networks and systems. Some common types of malware are viruses, worms, ransomware, and spyware.
The 2010 Stuxnet worm targeted Iran’s nuclear program and exploited zero-day vulnerabilities in Siemens software. It caused physical damage to centrifuges and demonstrated malware’s destructive potential as a cyber weapon.
2. Phishing
Phishing is a fraudulent attempt to obtain sensitive information, such as usernames, passwords, and credit card details, by posing as a trustworthy entity in electronic communication. Phishing can occur through emails, texts, or fake websites that capture personal data. Its subtypes are:
- Spear Phishing: Targets specific individuals or organizations, often using personalized information to make the attack more convincing.
- Whaling: A higher-level form of Spear Phishing, focusing on C-level executives or government officials, making it more strategic and damaging.
The 2016 John Podesta email hack, where a phishing email compromised the Hillary Clinton campaign chairman’s account, had significant ramifications during the U.S. presidential election, highlighting the high stakes of phishing attacks.
3. Denial of Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
DoS and DDoS attacks aim to overload a system or network with traffic, making services unavailable. A DoS attack involves a single source flooding the target, causing it to crash or become unresponsive. DDoS attacks are more complex, using multiple compromised systems (botnets) to conduct a coordinated attack. These attacks can take down websites, disrupt online services, and cause significant financial and reputational damage to the target organization.
The 2000 Yahoo! DDoS attack caused a massive traffic flood that took the search engine giant offline for nearly an hour, demonstrating the vulnerability of even the most prominent companies to coordinated cyberattacks.
4. Man-in-the-Middle (MitM) Attacks
MitM attacks involve eavesdropping on communication between two parties, stealing information, or injecting malicious code. These attacks aim to intercept sensitive information like login credentials, financial data, and personal communications. These attacks can occur as follows:
- Session Hijacking: The attacker takes control of an active session.
- IP Spoofing: The attacker falsifies an IP address to impersonate another machine.
The NSA PRISM program, where MitM techniques were allegedly used to intercept communications globally, raised serious privacy and surveillance concerns.
5. SQL Injection
SQL Injection occurs when a hacker inserts malicious SQL queries into input fields to manipulate a database. This attack can lead to unauthorized access to sensitive data, data modification, or even complete administrative control of the database. SQL Injection is one of the most dangerous web application vulnerabilities, often exploited to steal confidential data.
The 2008 Heartland Payment Systems breach involved an SQL injection attack that stole over 130 million credit card numbers, making it one of the largest data breaches in history.
6. Password Attacks
Password attacks involve systematically guessing passwords. These attacks can include Dictionary Attacks, which use common passwords from predefined lists, or Credential Stuffing, where attackers use breached usernames and passwords across multiple systems. Password reuse can lead to widespread compromise from a single breach. This malicious activity often targets social media accounts, as most users prefer reusing passwords across different platforms.
The 2012 LinkedIn breach, in which hackers stole over 117 million login credentials, highlighted the risks associated with password reuse. The stolen credentials were later used in credential-stuffing attacks across multiple platforms.
7. Social Engineering Attacks
Social Engineering attacks exploit human psychology to trick individuals into revealing confidential information. Methods include Pretexting (attackers create a fictitious scenario), Baiting (offering something enticing, e.g., USB drives, leading to malware installation), and Tailgating (attacker physically follows someone into a restricted area).
The 2013 Target data breach used social engineering tactics to access the retailer’s network, compromising 40 million credit and debit card accounts during the holiday shopping season.
Consequences of Cyber Attacks
The most critical consequences of cyberattacks include data breaches, reputation damage, operation disruption, and legal and regulatory repercussions. Their impact can result in substantial financial loss and infiltrate various business aspects.
Data Breaches
One of the worst outcomes of a cyberattack is a data breach involving the theft of sensitive information such as personal data, intellectual property, and other proprietary business data. Data breaches expose sensitive information and can result in significant financial losses from regulatory fines, legal settlements, and security remediation expenses. Additionally, the long-term reputational damage from customer data leakage can be severe and complex to recover from.
Reputation Damage
Apart from financial hits, reputation damage is another critical impact of cyberattacks. If consumers lose confidence in a company’s ability to secure their data, they may lose business, experience a decline in stock value, and struggle to acquire new customers. The negative publicity from a cyberattack can linger for years, harming the organization’s brand image and stakeholder confidence.
Operational Disruptions
Cyberattacks often lead to operational disruptions such as downtime, service interruptions, or even system-wide shutdowns. These disruptions can severely damage business operations, leading to lost revenue, decreased productivity, and an inability to serve customers. In sectors where uninterrupted service is crucial, downtime could be catastrophic, affecting everything from supply chains to customer service.
Legal and Regulatory Consequences
Non-compliance with data protection laws like the General Data Protection Regulation (GDPR) can result in severe legal and regulatory issues. Companies may face heavy fines, lawsuits, and investigations for failing to protect customer data. Beyond immediate penalties, extended litigation and increased expenses due to compliance and remediation can follow.
Cybersecurity Measures to Prevent Cybersecurity Risk
Robust cybersecurity strategies, such as prevention, detection, response, and education, are critical to reducing cybersecurity risks. These measures help protect against current and future cyber threats and attacks.
Prevention Strategies
Preventive measures are the frontline defense against cyberattacks. Firewalls are barriers between trusted internal networks and external threats, while antivirus software detects and removes malicious programs. Robust authentication methods like multi-factor authentication (MFA) ensure that only authorized users can access sensitive systems. Regular security audits also help identify and fix vulnerabilities before they are exploited.
Detection Systems
When prevention fails, detection systems play a vital role in identifying threats. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are essential for monitoring network traffic for potential intrusions. IDS identifies and alerts administrators to threats, while IPS blocks malicious activity in real time. These systems are critical for early detection and response to cyber threats.
Incident Response
A strong incident response plan is essential when prevention and detection fail. This plan outlines how to respond during an attack, including identifying the breach, stopping further damage, removing the threat, and restoring affected systems. An effective incident response will help minimize downtime and data loss, allowing organizations to return to normal operations quickly.
Cybersecurity Services
Outsourcing cybersecurity services from a reputable IT company, generally a Managed Service Provider (MSP), like CloudAvize, is a smart strategy for many organizations. Businesses lacking an in-house team can get deep knowledge and resources to strengthen their security posture. These solutions offer comprehensive protection, from managed security services to advanced threat detection and response against cyber threats.
User Awareness and Training
Human error is responsible for a significant percentage of security breaches. User awareness and training to identify phishing and other social engineering attempts are the most effective ways to prevent such exploits. Regular training sessions and simulated phishing exercises ensure that all users are up to date on best practices and keep security at the forefront of their minds.



