Cybersecurity as a Service (CSaaS) involves third-party vendors delivering comprehensive security solutions to safeguard organizations against cyber threats. With the global annual cost of cybercrime predicted to reach $9.5 trillion USD in 2024 and damages expected to hit $10.5 trillion by 2025, the importance of robust cybersecurity measures is more critical than ever.
CSaaS offers functionalities including initial setup, continuous monitoring, threat prevention, incident response, post-incident analysis, and continuous improvement. It encompasses various types of cybersecurity services such as network security, endpoint security, cloud security, data security, application security, and Managed Detection and Response (MDR). The benefits of CSaaS are substantial, including cost reduction, pre-emptive planning, centralized management, automated threat detection, and scalability.
In this article, we will explore the detailed functionalities of CSaaS, examine the different types of cybersecurity services, highlight the key benefits, and outline the costs involved, including subscription fees and customization expenses.
Table of Contents
What Is Cybersecurity as a Service (CSaaS)?

Cybersecurity as a Service (CSaaS) is a managed security solution where third parties provide services like continuous monitoring, threat detection, and incident response. It is crucial in today’s digital landscape, with the global cybersecurity market valued at over $190 billion and expected to reach $298.5 billion by 2028, growing to $538.3 billion by 2030. CSaaS relies on the security vendor’s dedicated Security Operations Center (SOC) for 24/7 managed security, offering an outsourced model of cybersecurity management.
The key entities in CSaaS are the CSaaS Provider and the CSaaS Model. The provider is responsible for managing the cybersecurity infrastructure, while the model operates on a subscription basis, offering scalable and flexible cybersecurity services. This approach allows organizations to leverage advanced security technologies and expert resources without maintaining an in-house team.
What is Cybersecurity as a Service Model?
Cybersecurity as a Service Model is a subscription-based framework where organizations get top-tier security services, advanced software, and expert human oversight into a comprehensive solution. This model provides adaptable, scalable security solutions tailored to the organization’s specific requirements, enabling them to adjust their defenses accordingly.
The CSaaS model delivers cost-effectiveness by eliminating the need for significant upfront investments in cybersecurity infrastructure and personnel. It provides access to advanced cybersecurity technologies and expertise, enabling organizations to leverage state-of-the-art security solutions and skilled professionals without maintaining an in-house team.
Who is a CyberSecurity as a Service Provider?
A CyberSecurity as a Service (CSaaS) provider is a third-party organization that manages and secures a company’s digital assets, including data, networks, and systems. These providers offer expertise, advanced security software, and experienced cybersecurity professionals to protect against cyber attacks. They implement measures like multi-factor authentication, encryption, intrusion detection systems, endpoint protection, and regular security audits to safeguard digital assets from unauthorized access and data breaches.
CSaaS providers deliver services through continuous monitoring, threat detection, and incident response. They use tools such as firewalls and machine learning algorithms to monitor network activities around the clock, identify potential threats, and respond promptly to security incidents. By providing comprehensive cybersecurity solutions, these providers allow companies to focus on their core business operations without worrying about cyber threats.
How CSaaS Differs From Traditional In-house Cybersecurity?
CSaaS differs from traditional cybersecurity by being proactive with continuous monitoring and pre-emptive threat mitigation, as opposed to the reactive approach of dealing with issues only after they occur. The proactive nature of CSaaS ensures ongoing threat prevention, unlike in-house cybersecurity, which typically responds post-incident. This continuous vigilance significantly reduces the risk of breaches and minimizes potential damage.
CSaaS provides access to specialized resources and expertise, offering a more comprehensive and robust solution compared to in-house teams. Additionally, CSaaS is cost-effective and scalable, avoiding the higher costs and limited scalability associated with maintaining an in-house cybersecurity team. Organizations benefit from the latest security technologies and practices without the need for significant investments in infrastructure and training.
How Cybersecurity as a Service Works?
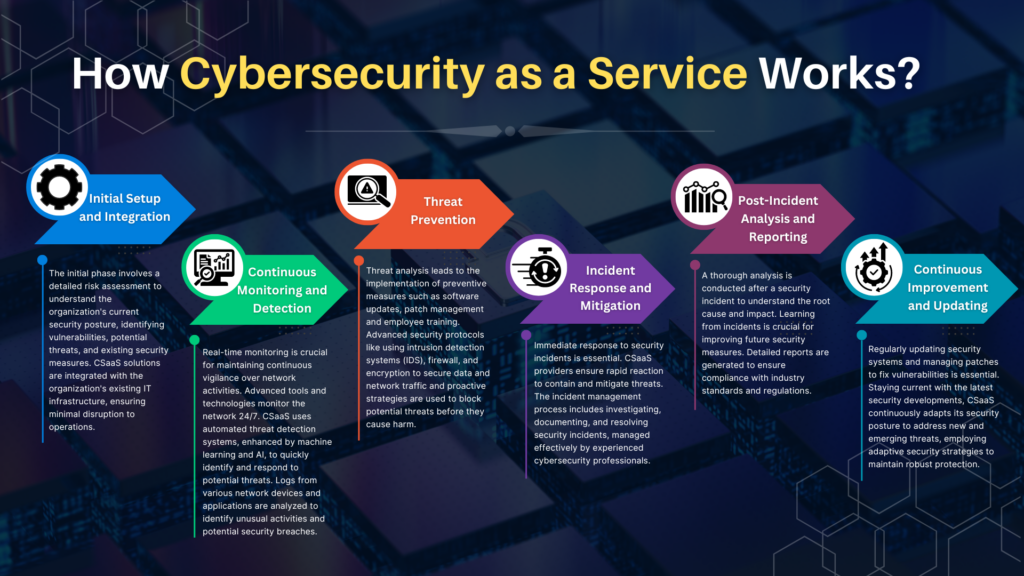
Cybersecurity as a Service (CSaaS) works through a structured, multi-phase approach to ensure comprehensive protection against cyber threats. It starts with a detailed risk assessment to understand the organization’s current security posture, identifying vulnerabilities and potential threats.
CSaaS solutions are then integrated with the existing IT infrastructure with minimal disruption. Continuous real-time monitoring and automated threat detection systems are deployed to identify and respond to potential threats. Preventive measures are implemented to block threats before they cause harm. In case of security incidents, CSaaS providers ensure rapid response and mitigation, followed by post-incident analysis to improve future security measures. Regular updates and patch management keep the system protected against emerging threats.
Here is a detailed working process of a CSaaS:
- Initial Setup and Integration
The initial phase involves a detailed risk assessment to understand the organization’s current security posture, identifying vulnerabilities, potential threats, and existing security measures. CSaaS solutions are integrated with the organization’s existing IT infrastructure, ensuring minimal disruption to operations.
- Continuous Monitoring and Detection
Real-time monitoring is crucial for maintaining continuous vigilance over network activities. Advanced tools and technologies monitor the network 24/7. CSaaS uses automated threat detection systems, enhanced by machine learning and AI, to quickly identify and respond to potential threats. Logs from various network devices and applications are analyzed to identify unusual activities and potential security breaches.
- Threat Prevention
Threat analysis leads to the implementation of preventive measures such as software updates, patch management and employee training. Advanced security protocols like using intrusion detection systems (IDS), firewall, and encryption to secure data and network traffic and proactive strategies are used to block potential threats before they cause harm.
- Incident Response and Mitigation
Immediate response to security incidents is essential. CSaaS providers ensure rapid reaction to contain and mitigate threats. The incident management process includes investigating, documenting, and resolving security incidents, managed effectively by experienced cybersecurity professionals.
- Post-Incident Analysis and Reporting
A thorough analysis is conducted after a security incident to understand the root cause and impact. Learning from incidents is crucial for improving future security measures. Detailed reports are generated to ensure compliance with industry standards and regulations.
- Continuous Improvement and Updating
Regularly updating security systems and managing patches to fix vulnerabilities is essential. Staying current with the latest security developments, CSaaS continuously adapts its security posture to address new and emerging threats, employing adaptive security strategies to maintain robust protection.
5 Different Types of Cybersecurity Services
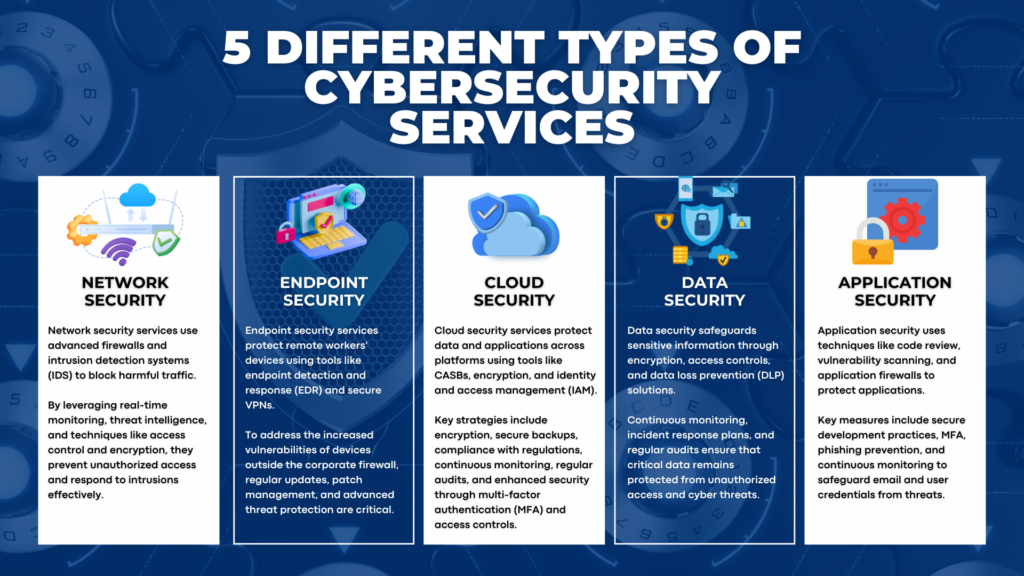
There are five different types of cybersecurity services designed to protect various aspects of an organization’s digital infrastructure: Network Security, Endpoint Security, Cloud Security, Data Security, and Application Security. Each service addresses unique threats and employs specific strategies to ensure comprehensive protection. These services work together to provide a robust security framework, safeguarding all entry points and data within the organization. By leveraging these specialized services, organizations can effectively mitigate risks and enhance their overall cybersecurity posture.
- Network Security
Network security services block harmful traffic using advanced firewalls and intrusion detection systems (IDS). Real-time monitoring and threat intelligence play crucial roles in identifying and neutralizing threats. Network security measures prevent unauthorized access by employing techniques like access control, encryption, and network segmentation. Continuous network monitoring is essential to detect and respond to intrusion attempts effectively.
- Endpoint Security
Endpoint security services protect devices used by remote workers, ensuring secure connections and safeguarding sensitive data. These services use endpoint detection and response (EDR) tools and secure VPNs to maintain security. Securing devices outside the corporate firewall presents challenges, such as increased vulnerability to attacks. Regular updates, patch management, and advanced threat protection are essential to keep these endpoints secure.
- Cloud Security
Cloud security services protect data and applications across multiple cloud platforms. These services use cloud access security brokers (CASBs), encryption, and identity and access management (IAM) to ensure secure cloud environments. Strategies to protect data stored in the cloud include data encryption, secure backup solutions, and compliance with regulatory standards. Regular security audits and continuous monitoring are also essential to identify and address vulnerabilities. Multi-factor authentication (MFA) and robust access controls further enhance the security of cloud-based resources.
- Data Security
Data security involves securing sensitive data through encryption, access controls, and data loss prevention (DLP) solutions. Data security services prevent breaches by implementing robust security policies, continuous monitoring, and incident response plans. These measures ensure that sensitive information remains protected from unauthorized access and potential cyber threats. Regular audits and updates to security protocols further enhance the protection of critical data assets.
- Application Security
Application security involves techniques such as code review, vulnerability scanning, and application firewalls to secure applications. Secure development practices and regular updates are crucial for maintaining application security. Specific measures to protect email and user credentials include multi-factor authentication (MFA), phishing prevention, and secure email gateways. Continuous monitoring and threat intelligence play a vital role in preventing credential theft.
How Does Managed Detection and Response (MDR) Fit into CSaaS?
Managed Detection and Response (MDR) services within CSaaS continuously monitor network activities to detect potential threats in real-time. MDR services use advanced tools and technologies to identify suspicious activities and potential security breaches, ensuring threats are detected early.
Once a threat is detected, MDR services respond immediately to neutralize it. The rapid response is crucial to minimizing damage, and cybersecurity professionals manage incidents effectively. Their expertise ensures threats are contained and resolved quickly, maintaining the integrity and security of the organization’s network.
What Are the Key Benefits of CSaaS?
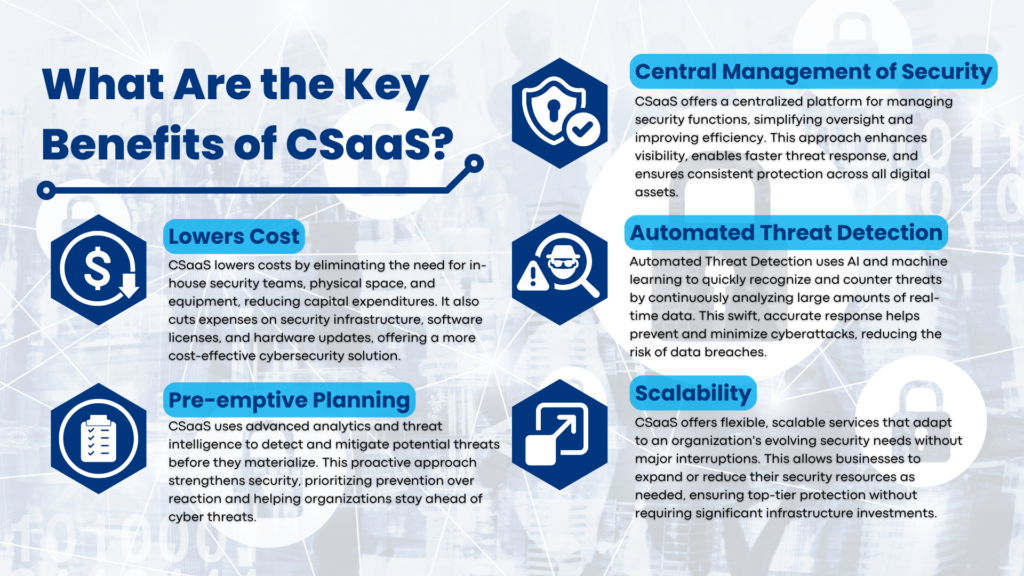
Cybersecurity as a Service (CSaaS) offers numerous benefits to organizations, including cost reduction, pre-emptive planning, centralized security management, automated threat detection, and scalability. CSaaS provides continuous monitoring and expert management, ensuring real-time threat detection and response. It leverages advanced security technologies that are often too costly for individual organizations to implement.
By outsourcing cybersecurity, organizations can focus on their core business activities while maintaining robust security measures. CSaaS adapts to the evolving threat landscape, providing up-to-date protection against emerging cyber threats. These benefits make CSaaS an attractive option for businesses seeking robust and efficient cybersecurity solutions.
Let’s take a look at five crucial benefits Cybersecurity as a Service offers:
- Lowers Cost
CSaaS lowers costs by eliminating the need for maintaining in-house cybersecurity teams, physical space, and equipment. This reduction in overhead significantly decreases capital expenditures. Organizations save on salaries, benefits, and ongoing training costs associated with in-house security.
CSaaS also reduces expenses related to purchasing and maintaining security infrastructure. The cost savings extend to software licenses and hardware updates. Overall, CSaaS provides a more cost-effective solution for comprehensive cybersecurity.
- Pre-emptive Planning
CSaaS leverages advanced analytics and threat intelligence to detect potential threats before they materialize. Pre-emptive planning minimizes risks by identifying vulnerabilities early. This strategic approach anticipates and mitigates potential security threats effectively.
By staying ahead of cyber threats, CSaaS helps organizations maintain a robust security posture. Proactive planning ensures continuous protection and reduces the likelihood of successful attacks. Organizations benefit from a forward-thinking approach that prioritizes prevention over reaction.
- Central Management of Security
CSaaS provides a centralized platform for managing all security functions, ensuring streamlined and efficient security operations. This single point of control simplifies oversight, making it easier to manage and coordinate various security tasks. Central management enhances visibility and accountability, ensuring comprehensive protection across the organization.
The centralized approach of CSaaS allows for faster response to threats and incidents, reducing potential damage. It also facilitates the integration of advanced security tools and technologies, improving overall security posture. Organizations benefit from consistent security policies and practices, ensuring uniform protection across all digital assets.
- Automated Threat Detection
Automated Threat Detection combines machine learning and AI to recognize and counter threats quickly. Automation analyzes a huge chunk of real-time data continuously and improves threat detection ability. As a result, the enhanced accuracy helps identify potential security issues faster compared to manual methods.
Automated systems offer an increased response in threat detection, which aids in restricting probable damage. This swift action system becomes essential in avoiding and minimizing cyberattacks, which prevents data breaches.
- Scalability
Depending on the organization’s security needs and evolution, the CSaaS solution can easily scale its services. It allows companies to manage their cybersecurity resources adeptly without major interruptions. Businesses can expand their security needs with their growth and reduce accordingly while downsizing via their CSaaS provider.
The flexibility provided by the CSaaS provider accommodates an organization’s growth and changes while keeping its security measures intact and operational. Businesses choose service providers who can keep up with the dynamic market conditions while offering adaptable security solutions. This flexibility ensures top-tier security protection without any need for investment in infrastructure overhaul.
How Much Does Cybersecurity as a Service Cost?
Cybersecurity as a Service (CSaaS) costs between $2,000 and $3,500 per month, depending on the scope and complexity of the required services. The cost factors encompass the size, security needs, requirements, and level of service needed by a business.
The CSaaS provider offers its services in four different models: subscription, monthly, quarterly, and annual plans. Each model can be customized per the client’s requirements, providing flexibility to meet organizational goals. This model saves an organization’s money and resources by helping them avoid the establishment of an in-house team, hence offering an affordable and scalable alternative.
Why Outsourcing Cybersecurity Is a Cost-Effective Strategy?
Outsourcing cybersecurity through CSaaS is a cost-effective strategy because it reduces both direct and indirect costs compared to maintaining an in-house team. Direct costs such as salaries for specialized staff, training programs, and purchasing advanced security equipment are minimized. Indirect costs, including ongoing maintenance and the need for continuous upgrades, are also significantly lower with CSaaS.
Outsourcing cybersecurity allows better resource allocation, enabling organizations to focus on core business activities while security experts manage cyber threats. This approach provides peace of mind for business leaders, knowing that their digital assets are protected by experienced professionals using the latest technologies and best practices. The return on investment (ROI) for outsourced cybersecurity is higher, as it provides comprehensive protection, access to the latest technologies, and expert management at a fraction of the cost of in-house solutions. This strategy not only ensures robust security but also enhances overall operational efficiency.
What Qualifies as a Right CSaaS Provider?
The right CSaaS provider offers 24/7 security and monitoring capabilities, ensuring continuous threat detection and response. Round-the-clock protection is crucial for minimizing risks and maintaining robust cybersecurity.
Industry-leading SLAs and fast response times are essential qualifications for a top CSaaS provider. These factors ensure effective incident management and minimized downtime, which are vital for maintaining business continuity and protecting sensitive data from prolonged exposure during incidents.
A top CSaaS provider utilizes advanced security technologies. Important tools include machine learning, artificial intelligence, and automated threat detection systems, which enhance the ability to identify and respond to sophisticated threats quickly and accurately.
Expertise and certifications are critical when choosing a CSaaS provider. Relevant certifications include CISSP, CISM, and ISO 27001, indicating a high level of professional competency and adherence to industry standards. These certifications demonstrate the provider’s commitment to maintaining up-to-date knowledge and practices in the rapidly evolving field of cybersecurity.
Examples of CSaaS in Action
Real-world case studies demonstrate the successful implementation of CSaaS, highlighting how organizations faced specific challenges such as frequent phishing attacks, ransomware incidents, and unauthorized access attempts, and how CSaaS solutions effectively addressed these issues. The real life case studies reveal measurable benefits such as reduced incident response times, improved threat detection rates, and substantial cost savings, illustrating the effectiveness of CSaaS in enhancing organizational cybersecurity. Here are some real-world CSaaS case studies:
- Financial Institution: In 2023, ransomware attacks in the finance industry surged by 64%, with 81% of organizations experiencing data encryption during incidents. Financial institutions can benefit from CSaaS by implementing continuous monitoring to detect threats in real time, advanced threat detection to identify and neutralize ransomware before it can encrypt data, and rapid incident response to contain and mitigate the impact of breaches. Additionally, CSaaS can provide regular security assessments and updates to ensure compliance with industry standards.
- Healthcare Provider: Healthcare providers saw the highest average cost of a data breach in 2023, reaching $10.93 million. CSaaS can be crucial for healthcare providers by offering robust data encryption to protect sensitive patient records, continuous monitoring to detect and respond to unauthorized access attempts, and compliance management to ensure adherence to healthcare regulations like HIPAA. CSaaS also provides incident response services to quickly address and mitigate breaches, minimizing downtime and patient data exposure.
- Retail Company: The retail sector faces significant threats, with the average breach costing $2.9 million. Retail companies can leverage CSaaS to protect consumer credit card information and personally identifiable information (PII) through real-time threat detection, secure payment processing systems, and endpoint protection for devices handling transactions. CSaaS solutions can also include automated response protocols to quickly contain and mitigate breaches, reducing the potential financial impact and maintaining customer trust.
- Educational Institution: Educational institutions face significant cyber threats, with software vulnerability exploitation and phishing accounting for 29% and 30% of attacks, respectively. CSaaS mitigates these risks through continuous monitoring, automated threat detection, and regular software updates. CSaaS solutions deploy advanced security protocols and regular updates to patch software vulnerabilities and educate staff and students on recognizing and avoiding phishing schemes. This proactive approach ensures a robust defense against prevalent cyber threats in the education sector.
Challenges and Solutions
- Frequent Phishing Attacks:
- Challenge: Institutions face frequent phishing attacks, compromising sensitive customer information.
- Solution: Implement advanced threat detection and continuous monitoring, along with employee training and enhanced email filtering.
- Ransomware Attacks:
- Challenge: Struggle with ransomware attacks, disrupting operations and threatening patient data security.
- Solution: Automated threat detection and rapid incident response protocols, including endpoint security and regular security audits, preventing further ransomware attacks and ensuring uninterrupted services.
- Unauthorized Access Attempts:
- Challenge: Unauthorized access attempts and data theft, affecting customer trust and sales.
- Solution: Integration of robust access controls and real-time network monitoring, identifying and mitigating threats.
- Malware Infections:
- Challenge: Frequent malware infections and unauthorized access to records.
- Solution: Deployment of comprehensive network security measures, including intrusion detection systems and enhanced firewall configurations, blocking malware and unauthorized access.
Measurable Benefits
Measurable benefits achieved through CSaaS include significantly reduced incident response times, allowing faster containment and mitigation of threats. Improved threat detection rates are another key benefit, with advanced analytics and continuous monitoring enhancing the ability to identify and respond to potential threats swiftly. Overall cost savings are substantial, as CSaaS eliminates the need for maintaining expensive in-house cybersecurity infrastructure and staff, reducing overhead costs. These benefits collectively enhance the security posture and operational efficiency of organizations, making CSaaS a valuable investment.



